



Recent Cyber Attacks Illustrates That Organizations Need A Cybersecurity Strategy secureflo.net

Since the first quarter of the year 2020 till now, the percentage of cyber crimes and data breaches has increased sharply. According to many surveys, nearly 75%-77% of data breaches occurred during the first few months of the COVID outbreak through successful phishing attempts.
According to NIST SP 800-150, a cyber threat is “any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), corporate assets, individuals, other organizations, or the Nation through an information system via unauthorized access, destruction, disclosure, or modification, and denial of service”.
Cyber Security is often compared to a cat-and-mouse game in which information technology professionals battle every day against newly discovered vulnerabilities and threats. Cyber Hackers have developed more complicated techniques of executing their attacks, forcing every organization and individual to continuously improve their cyber security prevention and defense mechanisms (Downs, 2018).
With change happening constantly these days, the cyber battlefield has become like a whac-a-mole game where every organization battles continuously against known and unknown threats. Rains (2013) states that the threat landscape has dramatically evolved over the past ten years in ways that have been challenging for organizations to understand, manage, and predict.
The successful SQL Slammer and Blaster worm attacks in 2003 motivated IT professionals to adopt tactics, tools, and strategies to adapt to the changing threat levels. In the wake of these, organizations began implementing host-based firewalls, I.T. security training, deploying security controls, antivirus solutions as the primary method of securing their data and managing threats.
Organized cyber crimes target advanced vulnerabilities and threats, and often involve well developed government espionage and cyber-warfare programs designed to attack organizations and governments. Hacktivists have also emerged, motivated by political gains and aimed at organizations attempting more insidious attacks that require constant vigilance.
There are numerous types of cyber threats — malignant activities designed to harm or take information, or to in any case upset responsibilities and administrations. Regardless of the sort or the beginning, cyber threats are a genuine risk to business well being and activities.
Cyber events include various internet activities to steal money and obtain personal and confidential data. The most common types of Cyber crime are Malware,Phishing and Ransomware:
1. A Malware Infection is the most common type of cyber threat. While it’s often employed for financial gain, malware is also used as a weapon by nation-states, as a form of protest by hacktivists, or to test the security posture of a system.
2. With Phishing, the user usually gets an email sent from what looks like an authentic source such as banks, well known companies, fashion apps, and so on. Phishing Emails contain a surreptitious link that redirects to a third-party website. Clicking on those links can result in sharing the data from the device you are using to the people behind that link/website.
3. Ransomware is a similar event with a twist. Like Phishing, the user receives an email containing every possible authentic sign and a link to download content. Once you click on a link, unknown software may install on your device . By the time the download has completed, the attackers have gotten access to your data.
Once attackers access your personal data, they decide what nefarious purposes they will use it for, often to earn themselves money.
Data security seeks to secure all data resources, including both print and computerized versions. A data security plan provides controls, techniques, and mechanisms to shield and protect your data A cyberattack can be completed in a mere 40 seconds. In the USA, every 39 seconds,a cyber event occurs.
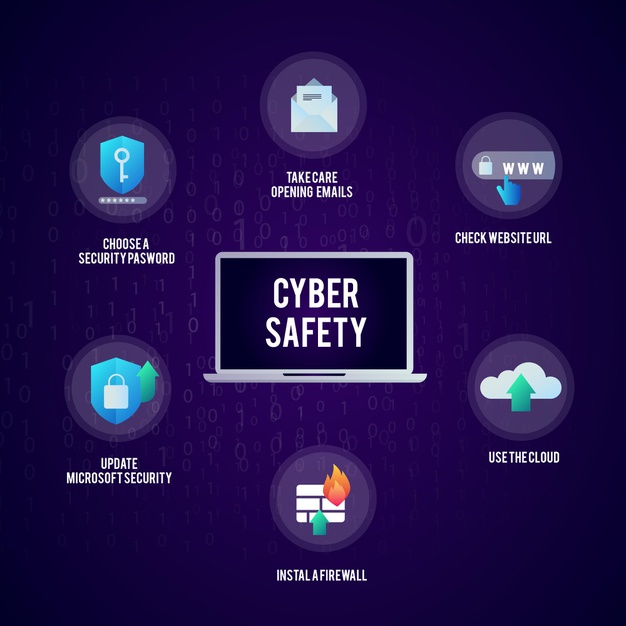
To prevent your organizational sensitive data from a cyberattack, a strong cybersecurity strategy should be implemented .Below are some data security measures that can help minimize the risk of cyber hacks.

1. Control Data Access: Restrict data access in your organization. Implement security controls that make use of least privilege to ensure access is given only to those who deserve it. Anyone who is not authorized will not be able to access the data. The confidentiality, integrity, and availability of data is primordial to the day-to-day operations.
2. Use Strong Password: It is always recommended to use an alphanumeric password to avoid hacking. Use a long password and avoid using the same code across multiple accounts.
3. Data Backup and Restore: Always create a duplicate of your data so that in an event of loss, malware attack or compromise, you will still have access to the alternate copy. According to reports, more than 68% of SMEs do not have a disaster recovery plan which is worrisome given the evident risk present in cyberspace.
4. Data Masking: Put an alphanumeric code on the data set in a way that your sensitive information gets hidden under the proxy alphanumeric code. Data masking is very effective in protecting sensitive data from being accessed, especially Personally Identifiable Information.
5. Regular System Update: Make sure to update your device and system on a regular basis. Older versions are easy to crack. Always implement software patches as they become available since hackers are on the lookout for zero-day attacks.
6. Install Firewall: Your first line of defense is a firewall. Firewall prevents your network system against an attacker by shielding malicious traffic from penetrating your network. You can take advantage of either hardware or software firewalls or both depending on what you aim to achieve.
7. Encryption: Data encryption is the process of encoding information into a form known as cipher text which can only be read by someone with the decryption key. When data is encrypted it becomes difficult for a man-in-the-middle attack to take place since the data appears scrambled.
8. Seek Professional Help: Finally, seek professional help from experts with cybersecurity and privacy experience. equipped with the know-how to provide data security services to your organization.
Primary Types of Cyber Security:
1. Application Security
2. Information Security
3. Infrastructure Security
4. Network Security
5. User Education
It is inevitable that practically every technology has a loophole. No matter how careful you are, your computer/mobile devices are never completely safe from getting hacked. Data security is mandatory to protect your organization’s sensitive data from being lost to cyber hackers Regardless of whether a cyber breach was malicious or unintentional, the outcome can be catastrophic to your organization and its reputation.Software can help manage your data and identify what data what to protect, from whom, and what data to purge when no longer necessary. You also should not over look the importance of data security when it comes to regulatory compliance. Without adequate data security, you’re putting yourself at risk in terms of fines and penalties which can be extensive.





